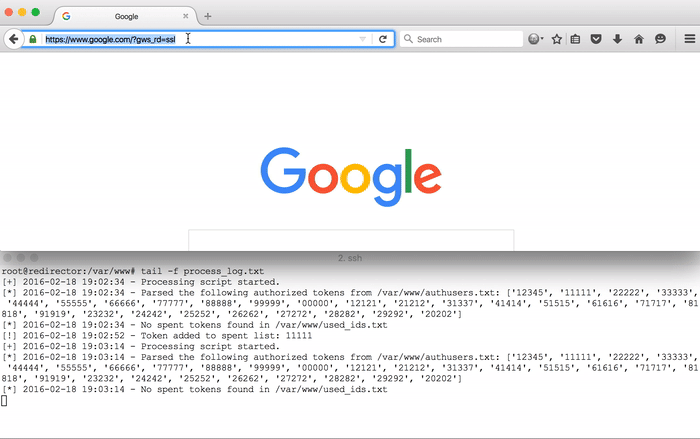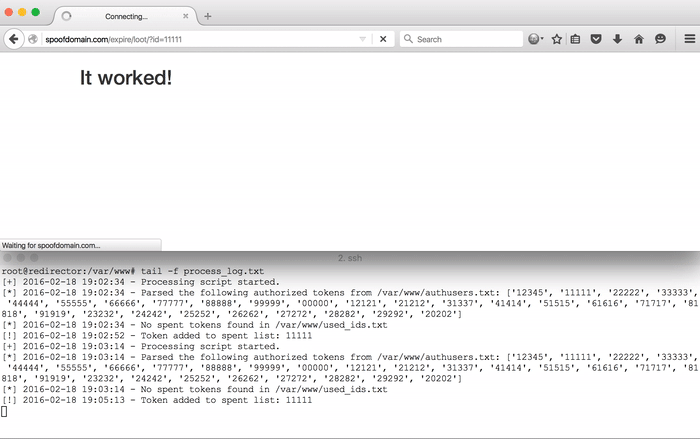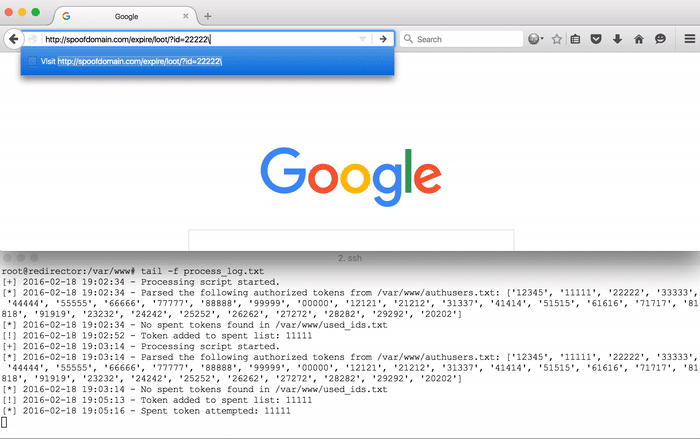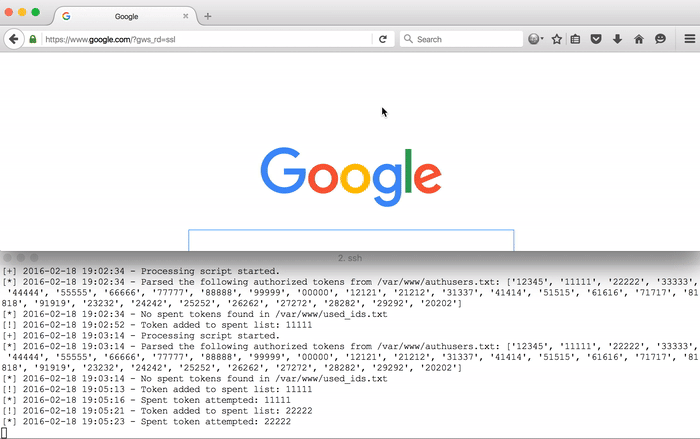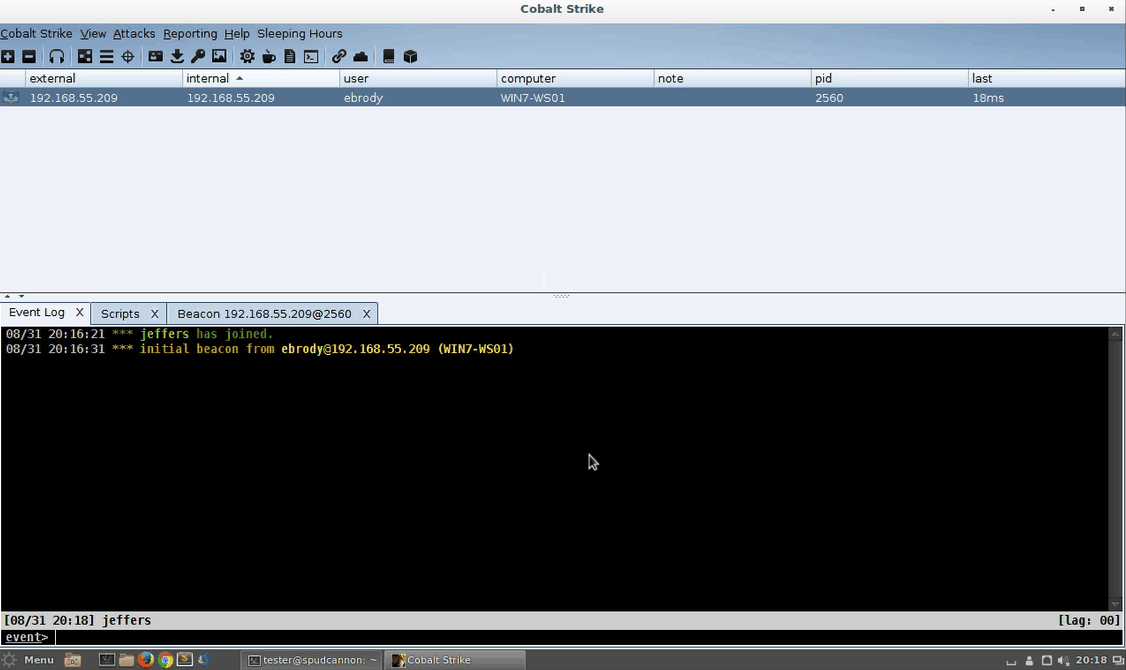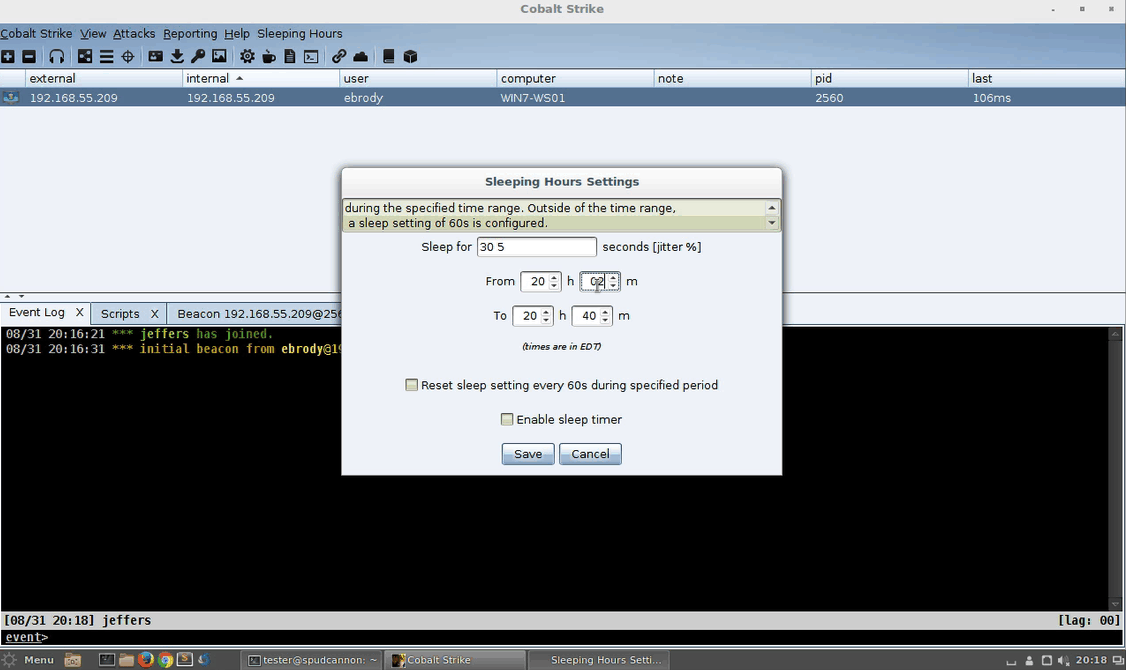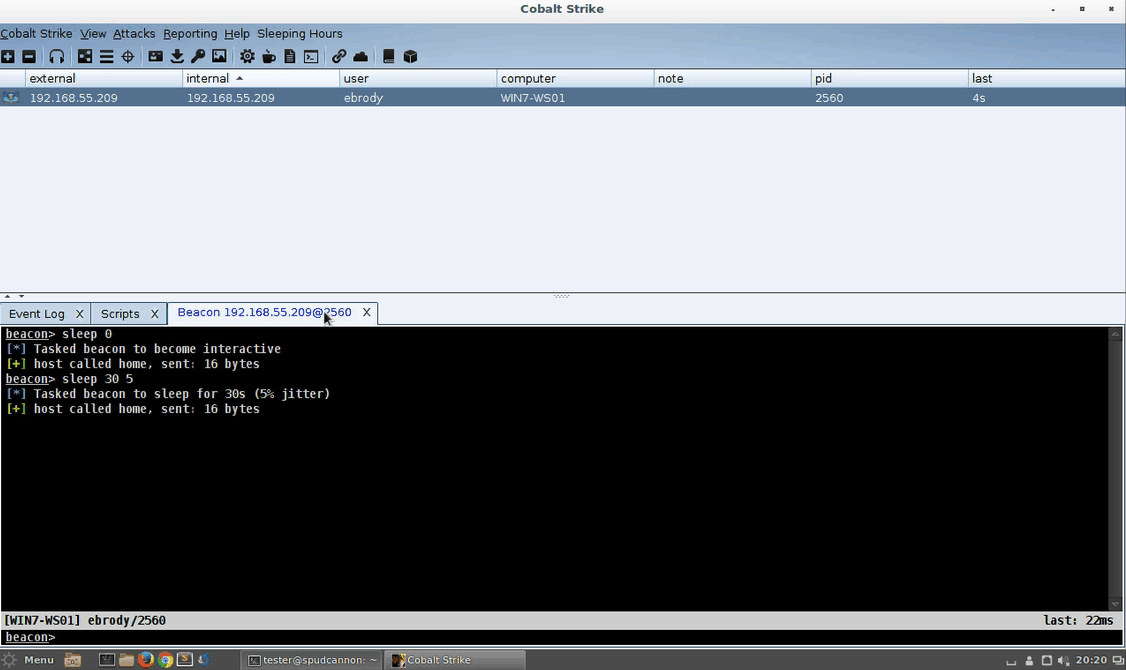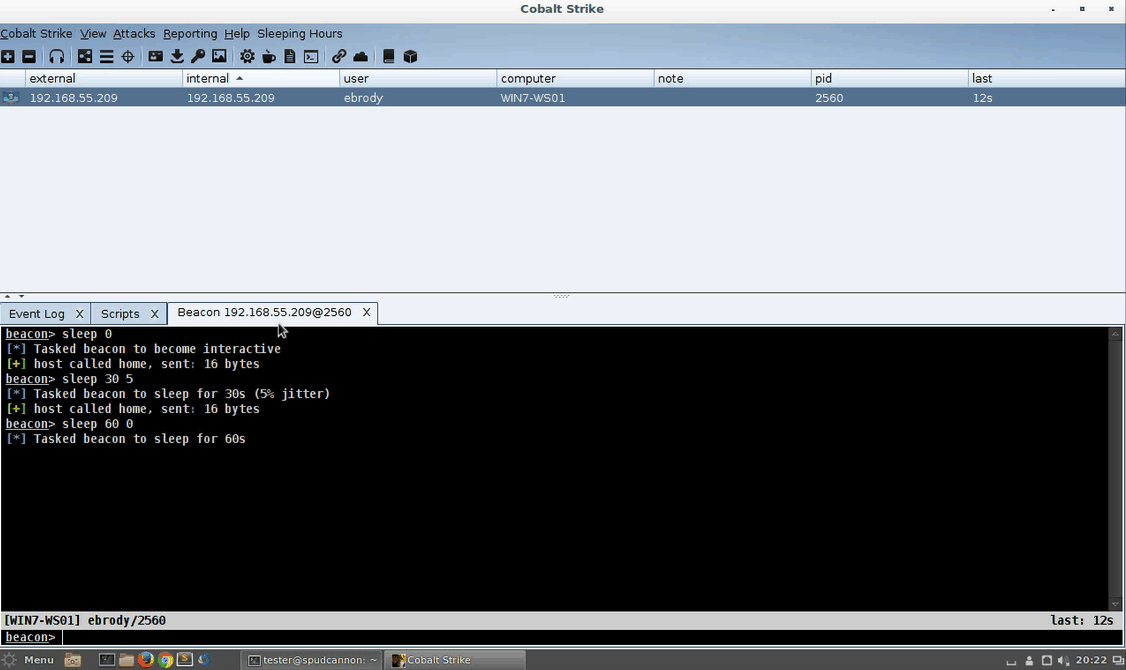
Adding Easy GUIs to Aggressor Scripts
As pentesters and red teamers, we have lots of commands floating around in our head. As much as the 1337 profess to hate GUIs, they sure do make testing a lot easier. Cobalt Strike provides testers a lot of power with an easy-to-use interface. Aggressor Script offers a wealth of extensibility options to expand Cobalt Strike’s built-in functions, but building out a custom GUI is a bit more difficult. Intro Cobalt Strike’s Aggressor Script is built upon Raphael Mudge’s Sleep language. As Raphael says, “Sleep is a Java-based scripting language heavily inspired by Perl,” and it includes the ability to create and access Java objects while still being an interpreted script. This means we can use a Java IDE with... [Read More]