How to Make Communication Profiles for Empire
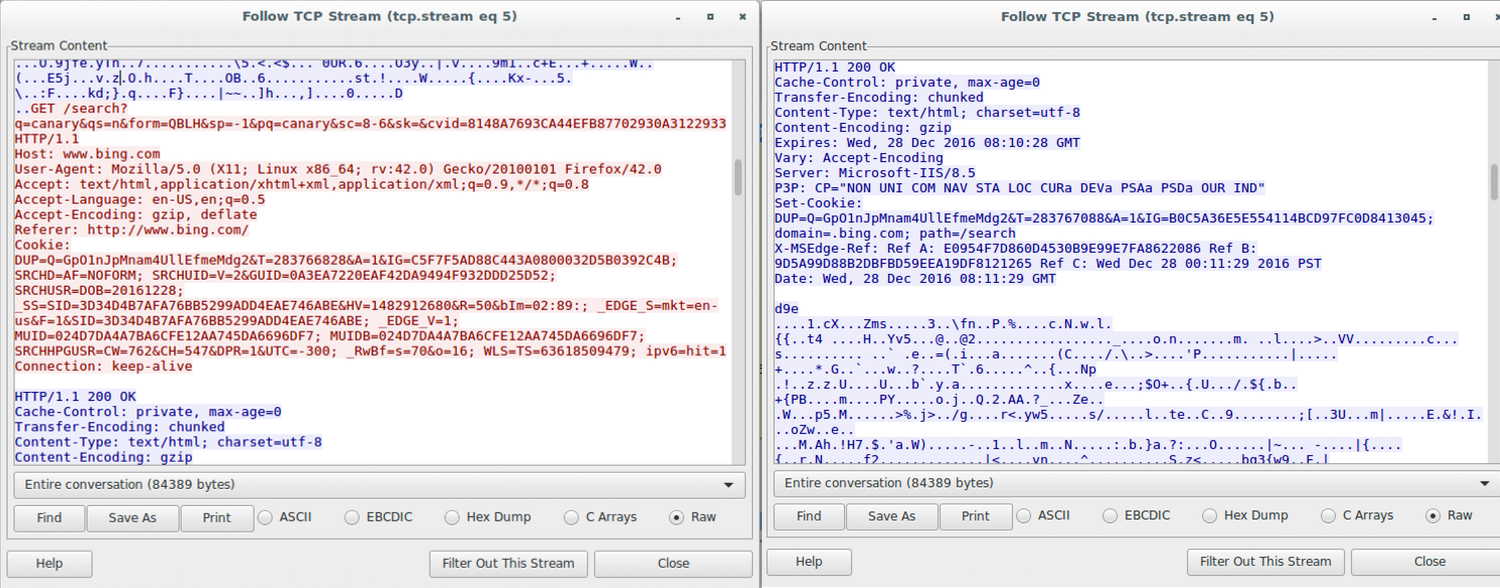
In a recent post, I detailed how to make a Malleable C2 profile for Cobalt Strike. Malleable C2 profiles provide an operator with the ability to shape how defenders will see, and potentially categorize, C2 traffic on the wire. Communication Profiles in Empire provide similar functionality. This increases our chances of evading detection, allows us to emulate specific adversaries, or masquerade as widely-used applications on our target’s network. Empire Communication Profiles With Communication Profiles, we can customize options for Empire’s GET request URIs, user agent, and headers. A basic profile consists of each element, separated by the pipe character, like this: GET request URI | User Agent | Header #1 Here is a sample profile for Comfoo:... [Read More]