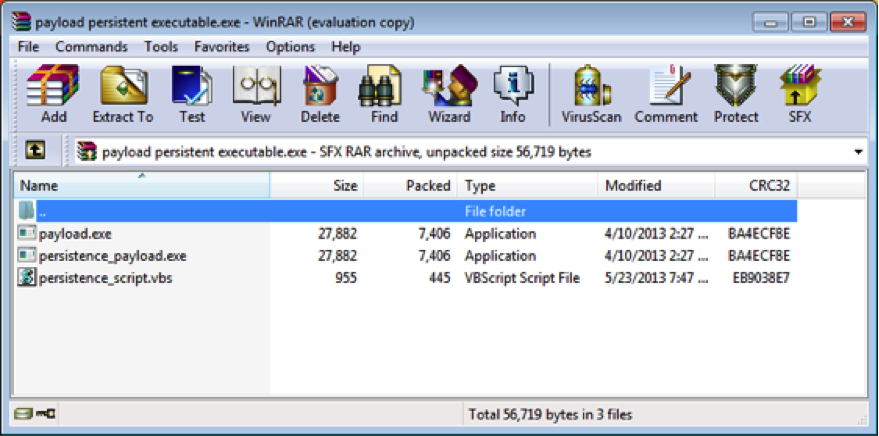
Making a Powershell EXE Payload
I’ve been using TrustedSec’s Unicorn a LOT over the past few months. In fact, it’s become my go-to payload to pop a box. While it’s awesome to be able to paste a command and get a shell, sometimes an EXE is required. For those cases, I’ve made a script to make the whole process automated: powershell_exe.py tl;dr powershell_exe.py uses winrar’s commandline options under wine to make a self-extracting archive. Source Setup instructions cd /opt git clone https://github.com/trustedsec/unicorn.git cd ~/Desktop wget http://www.rarlab.com/rar/wrar511.exe wine wrar511.exe Now just go through the default options of winrar to finish the install. Usage: python power_exe.py <payload>... [Read More]